| You should complete the Domain verification and Domain setup steps before completing this configuration. The links generated for the SSO configuration are built based on the Domain setup configuration. This will also allow you to manually add one of your users to test the SSO (SAML2) configuration after completing the configuration steps. These features are only available for premium service level licenses (Free 25 user Premium (for Partners only) and Premium (purchased by customer), it is not available for free and standard service level licenses.) |
The Security Awareness and Training Service allows customers and partners to share metadata to establish a baseline of trust and interoperability using the XML based Security Assertion Markup Language (SAML) standard.
Using one of your existing SAML2 single sign-on solutions to authenticate users when they log in to the system allows users to use an existing credential set (email / password / MFA (optional)) when logging in to the system. Users will not have to use a Fortinet assigned credential set (email / password / emailed MFA token) when logging in to the service.
| Configuring a single sign-on solution allows users to authenticate to the Fortinet Security Awareness and Training Service. Before users can log in, they must first be imported into the service. This is covered in a later chapter. Currently, the service does not support account creation during the single sign-on log in process. |
Different solution providers have different configuration steps for configuring a SAML2 app for authentication with third-party services. Customers will need to work with their internal IT department or service provider to configure the SAML2 application for the Fortinet Security Awareness and Training Service.
If you require assistance configuring the Authentication component, send an email to infosec_awareness@fortinet.com. A Deployment Specialist will reach out to request times that work and will schedule a meeting with our team, and, if necessary, the support team from your SSO vendor.
How to configure SSO - Adding Fortinet as a SAML service provider (SP)
1.) From the navigation menu, select Settings, then the Admin Setting sub-menu item:

2.) Select the Configure button in the Single Sign-On (SSO) section:

The configuration page is displayed:

3.) Select the Add Fortinet as a SAML service provider (SP) option button.
4.) In your SSO/SAML2 application configuration, copy and paste the Assertion Consumer service (ACS) URL and the Service Provider metadata (SP Entity ID) in the appropriate fields.
5.) Select the Continue button:
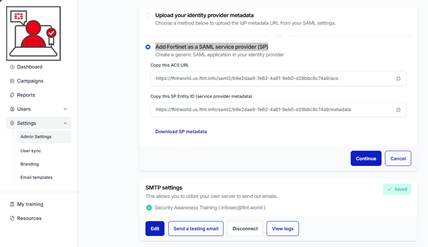
The Configure your SAML attributes screen is presented:
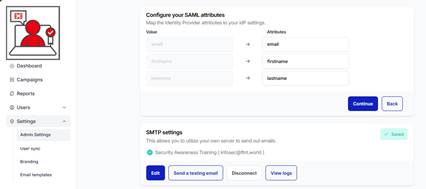
6.) Enter the SAML attributes you will configure in the third-party application. You can choose whatever name you desire, however, you must map the same attributes in your SAML application:
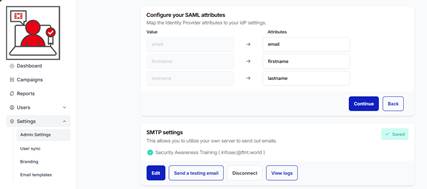
7.) Select the Continue button. The Upload your Identity Provider Metadata screen is presented:

You can cut and paste the Input metadata URL (e.g. Microsoft), Upload your Identity Provider Metadata (e.g. Google Workspace), or Configure the metadata manually using the matching values provided by your third-party application configuration.
| For Microsoft Entra/Azure/O365 implementations you must replace the IDP Logout URL under the Configure Manually tab with: https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 |
8.) Select the Complete button.
9.) You should now test that your custom url redirects to the configured provider login screen.
10.) Manually create a test user (you cannot use the Tenant Administrator account since it must use the FortiCloud SSO login) and verify that the user can log in via the third-party identity provider.
If you require assistance configuring the Authentication component, send an email to infosec_awareness@fortinet.com. A Deployment Specialist will reach out to request times that work and will schedule a meeting with our team, and, if necessary, the support team from your SSO vendor.
See the following articles for configuration of SSO/SAML2 for Microsoft Azure/Entra and Google Workspace:
(V3.x) How do I Configure SAML2 Single Sign-on (Authentication) to use Azure AD SSO? : Security Awareness and Training Service
(V3.x) How do I Configure SAML2 Single Sign-on (Authentication) to use Google Workspace SSO? : Security Awareness and Training Service
If you require assistance configuring the Authentication component, send an email to infosec_awareness@fortinet.com. A Deployment Specialist will reach out to request times that work and will schedule a meeting with our team, and, if necessary, the support team from your SSO vendor.
Name of User Profile Field | Mapped SAML Attributes | Examples |
Name ID Format | N/A | Google: Email |
Unique User Identifier (Microsoft only) | N/A | Microsoft: user.mail |
The name of the attribute varies depending on SSO/SAML2 solution (should be mapped to the primary email attribute). | Google: Email or Primary Email Microsoft: user.mail | |
First_name | The name of the attribute varies depending on SSO/SAML2 solution (should be mapped to the primary First Name attribute). | Google: First Name Microsoft: user.givenName |
Last_name | The name of the attribute varies depending on SSO/SAML2 solution (should be mapped to the Last Name attribute). | Google: Last Name Microsoft: user.surname (or sn) |
If you wish to configure access to the service through the user apps (Microsoft and Google), sometimes called the Start URL, refer to this article: https://helpdesk.ftnt.info/en/support/solutions/articles/73000613866-how-do-i-configure-google-workspace-so-that-learners-can-access-the-security-awareness-and-training-s
You will need to open a ticket in order to get your tenant name. Email infosec_awareness@fortinet.com asking for your tenant name. The url will be: https://app.training.fortinet.com/local/bridge/launch.php?name=<tenant_name>
Ensure that you add the users you wish to access the app via your SSO/SAML2 configuration interface.
If you are getting errors when accessing the link, then your SAML2 configuration on the SSO solution is incorrect.
If you are able to access the log in page for your configured SAML2 SSO solution, but get errors when attempting to log in, then your attributes are likely not configured properly. To troubleshoot this issue, you can use Chrome and the SAML-tracer plug in to verify the correct attributes and attribute values are being passed. Follow the instructions in this article:
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article